The NIST Risk Management Framework (RMF) describes the process for identifying, implementing, assessing, and managing cybersecurity capabilities and services, expressed as security controls, and authorizing the operation of Information Systems (IS) and Platform Information Technology (PIT) systems. RMF replaces the DoD Information Assurance Certification and Accreditation Process (DIACAP).
Definition: The Risk Management Framework (RMF) brings a risk-based approach to implementing cybersecurity, supports cybersecurity integration early and throughout the system lifecycle, promotes reciprocity to the maximum extent possible, and stresses continuous monitoring.
Risk Management
Risk management is a continuous process that is accomplished throughout the life cycle of a system and should begin at the earliest stages of program planning. It is used as the foundation of the Risk Management Framework (RMF). The approach is an organized methodology for continuously:
- Risk Identification: identifying and measuring the unknowns;
- Risk Mitigation: developing mitigation options;
- Risk Mitigation Implementation: selecting, planning, and implementing appropriate risk mitigations; and
- Risk Tracking: tracking the implementation to ensure successful risk reduction.
Risk Management Framework (RMF) Stated Goals
The goals of the Risk Management Framework, as stated by the Defense Security Service (DSS), are:
- Improve information security
- Strengthen risk management processes
- Encourage reciprocity among federal agencies
Risk Management Framework (RMF) References
Manual: Defense Security Service (DSS) Assessment and Authorization Process Manual (DAAPM)
Main Publication: NIST Special Publication 800-37 RMF for Information Systems and Organizations
Instruction: DoD Instruction 8510.01 Risk Management Framework for DoD Systems – 19 July 2022
Website: Defense Security Service RMF
Risk Management Framework (RMF) Objectives
The objectives of the RMF process include: [1]
- Incorporating cybersecurity early and robustly in the acquisition and system development life cycle.
- Implementing a three-tiered approach to risk management that addresses risk-related concerns at the enterprise level, the mission and business process level, and the information system level.
- Providing a risk management methodology that gives organizations a true picture of vulnerabilities caused by non-compliant controls as it relates to other risk factors (e.g. likelihood, threat, and impact).
- Codifying system authorization reciprocity enables organizations to accept approvals by other organizations for interconnection or reuse of IT without retesting.
- Emphasizing information security continuous monitoring and timely correction of deficiencies, including active management of vulnerabilities and incidents.
Risk Management Framework (RMF) Tutorial
7 Steps of the Risk Management Framework (RMF)
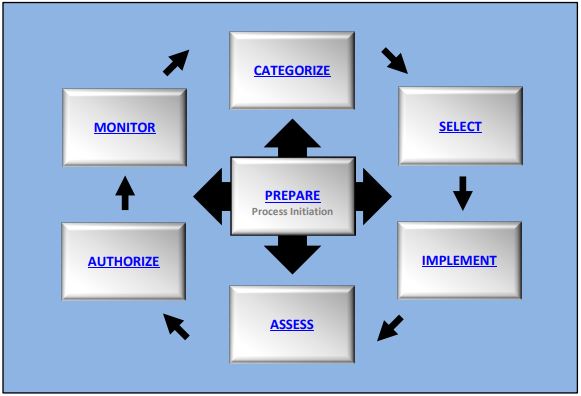
The RMF process parallels the defense acquisition process from initiation and consists of seven (7) steps: [1]
- Step 1: Prepare: Carry out essential activities at the organization, mission and business process, and information system levels of the enterprise to help prepare the organization to manage its security and privacy risks.
- Quick Guide: NIST RMF Prepare Step FAQs
- Step 2: Categorize System: Information Systems (IS) will be categorized based on the impact due to a loss of Confidentiality, Integrity, and Availability (CIA) of the information system (IS). Security impact levels are defined as Low, Moderate, or High. The impact values will be documented in the Security System Plan (SSP) along with the research, key decisions, approvals, and supporting rationale.
- Quick Guide: NIST RMF Categorize Step FAQs
- Step 3: Select Security Controls: Identify the security controls that are provided by the organization as common controls for all or multiple IS under the organization’s control and document the controls in the SSP. Control implementation can be characterized as:
- System Specific: Security controls specific to an IS and the responsibility of the security officer.
- Common: Security controls that are inheritable by one or more organizational IS and are typically provided by the organization or the infrastructure (Examples: Physical and
environmental security controls, Network boundary defense security controls, Organization policies or procedures, etc.). - Hybrid: Security controls that are implemented in an IS in part as a common control and in part as a system-specific control. If any of the IS components need system-specific infrastructure protections, in addition to common controls that apply to the IS, the control is implemented as a hybrid control.
- Quick Guide: NIST RMF Select Step-FAQs
- Step 4: Implement Security Controls: Implement the controls in the security and privacy plans for the system and organization. Document all the processes and procedures you need.
- Quick Guide: NIST RMF Implement Step-FAQs
- Step 5: Assess Security Controls: Determine if the controls are implemented correctly and producing the desired outcome with respect to meeting the security and privacy requirements for the system and the organization.
- Quick Guide: NIST RMF Assess Step-FAQs
- Step 6: Authorize System: Provide formal authorization if everything is working as intended.
- Quick Guide: NIST RMF Authorize Step-FAQs
- Step 7: Monitor Security Controls: A continuous monitoring strategy is required to determine whether the security controls work. Continuous monitoring activities support the concept of near real-time risk management through ongoing security assessments and risk analysis and recording results in IS security documentation.
- Quick Guide: NIST RMF Monitor Step-FAQs
Risk Management Framework (RMF) Levels
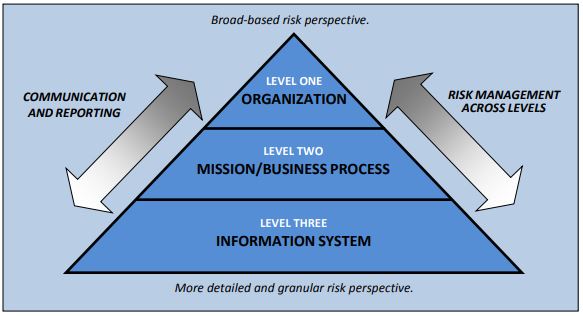
The DoD RMF governance structure implements a three-tiered approach to cybersecurity risk management.
- Tier 1 Strategic Level: Addresses risk management at the DoD enterprise level. At this tier, the DoD Chief Information Officer (CIO) directs and oversees the cybersecurity risk management of DoD IT. The Risk Executive Function is performed by the DoD Information Security Risk Management Committee (ISRMC).
- Tier 2 Mission / Business Processes Level: At this level, the Component CIO is responsible for the administration of the RMF within the DoD Component cybersecurity program.
- Tier 3 IS and PIT Systems Level: The DoD Component Heads are responsible for the appointment of trained and qualified Authorization Officials for all DoD ISs and PIT systems within their Component.
Risk Management Framework (RMF) Roles and Responsibilities
There are various roles and responsibilities for the development and execution of the risk management framework in any program. These roles and responsibilities are detailed in the RMF Roles and Responsibilities Crosswalk.
Presentation: NIST RMF Roles and Responsibilities Crosswalk
Utilize the Risk Reporting Matrix
The risk management plan should detail how to use the Risk Reporting Matrix to determine the level of risks identified within a program. This is a great tool for understanding the importance of which risks you should focus on to mitigate. The level of risk for each root cause is reported as low (green), moderate (yellow), or high (red). 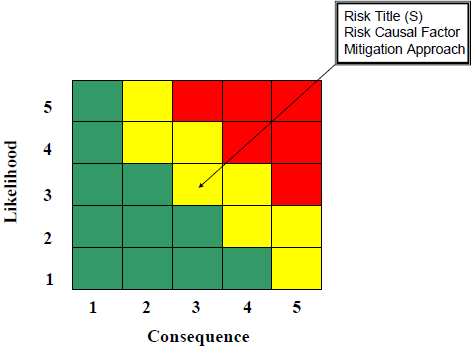
8 Key Areas to Understanding the Risk Management Framework (RMF)
A manager should remember a few key things when using a Risk Management Framework (RMF) in a project’s lifecycle. Here are a few things you should know:
- Identifying Risks: The project manager should know what the project’s goals, scope, and partners are. This information will help find possible risks that could affect the project’s success. Engaging stakeholders, holding brainstorming meetings, and looking at data from the past can all help find all the risks.
- Risk Assessment: Once risks have been found, they need to be evaluated to find out how bad they could be and how likely they are to happen. The manager should know how to do things like qualitative analysis (which rates risks based on their likelihood and impact) and quantitative analysis (which uses numbers to rate the likelihood and impact of risks).
- Risk Planning: Based on the risk assessment, the manager should make a plan for how to deal with risks. This plan lists the exact steps that need to be taken to reduce, transfer, accept, or avoid risks that have been identified. It’s important to include the right people in this process of planning to get their buy-in and help.
- Risk Monitoring and Control: The project manager should keep an eye on the risks that have been discovered and the plans for how to deal with them. Reviewing and updating risks regularly is important to see how well they are being dealt with and to spot any new risks that may come up. The risk management plan may need to be changed depending on how the project is going.
- Communication and Involvement of Stakeholders: A risk management system needs good communication and involvement of stakeholders. The manager should set up a plan for communicating with stakeholders to share information about risks, make sure they are aware of and understand risks and get their input and comments.
- Contingency Planning: The manager should think about making plans for high-impact risks that can’t be completely avoided. Plans for what to do if certain risks come true list other actions or methods that can be used. These plans give an organized way to deal with things that don’t go as planned.
- Lessons Learned: The manager should make sure that lessons learned during the job are written down and saved. This includes what we learned from risk events, how they affected us, and how well we handled them. The lessons learned are helpful for future projects and help the company get better at managing risks.
- Risk Culture and Proactive Approach: A manager should ensure that the project team and the company are aware of risks. By encouraging a proactive approach to risk management, pushing open conversations about risks, and giving team members the power to report and deal with risks, the project will be much better able to find and deal with risks.
By keeping these things in mind, a manager can use a Risk Management framework successfully throughout the lifecycle of a project. This proactive method helps reduce the bad effects of risks, make the most of opportunities, and improve the overall results of a project.
AcqLinks and References:
- DoD Instruction 8510.01 Risk Management Framework for DoD Systems – 19 July 2022
- (Old) DoDI 8510.01 “Risk Management Framework for DoD Information Technology” – 24 May 2016
- [1] Defense Security Service (DSS) Assessment and Authorization Process Manual (DAAPM) – 4 Jun 2018
- NIST Special Publication 800-37 RMF for Information Systems and Organizations – Revision 2
- Risk Management Framework FAQ – April 2018
- NIST RMF Roles and Responsibilities Crosswalk
- Article: The Cybersecurity and Acquisition Life-Cycle Integration Tool by Steve Mills and Tim Denman
- Website: Defense Security Service RMF
Updated: 6/30/2023
Rank: G12.8
